Nothing can be as annoying as having a dysfunctional or problematic computer device as a result of viruses and malware. Computer viruses are most often spread over the internet, by attachments in emails, by instant messaging, and other such platforms. It is safer that you never open an email attachment unless you know exactly who sent you the email or you are expecting the email attachment. Viruses can be disguised as attachments of funny images, greeting cards, or audio and video files, etc. Malware and viruses in the computer also spread through use of, and downloads from the Internet. Cyber-criminals can have them hidden in pirated software or in other files or programs that you would naturally download; hackers and cyber-criminals have perfected the art of getting unsuspecting users to pick up malware and viruses every day on the internet and also even offline. It is therefore imperative that users must be a lot more vigilant and always stay updated and ahead of the game if we must survive under such conditions. Avast Free Antivirus is one of the very reliable tools with which you can stay safe from hackers and cyber-criminals.
Computer Viruses
A computer virus is a small software program that spreads freely from one computer to another and interferes with or feeds off from infected computer(s) daily operations. Computer viruses are usually designed to do several harmful things to their host computers including corrupting or deleting data on the infected computer, using any available email program to continue spreading the virus to other nearby computers or even totally wipe off everything on the hard disk, and so on.
Spywares

Spywares can find their way into your computer and gain permissions without your knowledge. As a result, these programs can change your computer’s original configuration; collect advertising data, personal information, etc. Spyware can track Internet search habits, they can also redirect your web browser to a different website than you intend to go to and quickly send and receive the information they want within split seconds.
Trojan Horses
A trojan horse is malicious software that hides inside other programs. It gains access to a computer by hiding inside other legitimate programs, such as a screensaver, wallpaper apps, games, etc. It then inputs codes into the infected operating system that enables a hacker to remotely access the infected computer. Trojan horses do not usually spread by themselves. They are spread by viruses, worms, and other downloaded software.
Worms
A worm is a computer code that is capable of spreading and replicating itself on another computer without any user interaction between both computers. Most of the time, the worm can start out as a single email attachment that infects one computer when they’re opened, from there, the worm begins to scan the infected computer(s) for files, such as address books or temporary webpages, that contain email addresses. It then uses these addresses to automatically send infected email messages while running in the background of the infected computer. Also, it frequently mimics (or spoofs) the “From” addresses in subsequent email messages so that those infected messages appear to be from someone you know. Worms work seamlessly in the background by camouflaging themselves and then spread automatically through email messages, networks, or other operating system vulnerabilities that are apparently unnoticed by the user. A worm often overwhelms their infected systems, spread, and freely replicates itself long before they could ever be found, or traced, or even suspected. Worms are not always destructive to computers because they depend on the daily activities of the computer in order to thrive; however, they are capable of causing computer and network performance and stability issues.
Rogue Security Software
A rogue security software program is one that tries to make you think that your computer has been infected by a virus. It typically prompts you to download or buy a product that can get rid of the virus. These products usually hid under the disguise of names like Antivirus, Shield, Avast Internet Security, Protection, Fixer, etc; this makes them sound legitimate and unsuspecting individuals would often voluntarily download them. They often run right after you download them, or the next time that your computer starts, during the booting process. Rogue security software can hinder applications, such as Internet Explorer, from opening. They might also display legitimate and important Windows files as infections. Typical error messages or pop-up messages might contain such phrases as:

Note: If you receive messages in a popup dialog box that resembles the one illustrated above, press ALT + F4 on your keyboard to close the dialog box. Do not click anything inside the dialog box! (They’re usually buggy trapped) If the warning, keeps appearing even after you have tried to close the dialog box using the “ALT + F4” command; it may continue to issue incessant warnings like the one below:
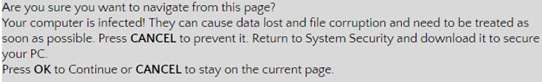
Are you sure you want to navigate from this page?
Your computer is infected! They can cause data loss and file corruption and need to be treated as soon as possible. Press CANCEL to prevent it. Return to System Security and download it to secure your PC.
Press OK to Continue or CANCEL to stay on the current page.
It’s a signal that the message is malicious.
Hence, if you notice this kind of notifications, then don’t download or buy the recommended software ─ it is a Rogue Security Software.
What Is Malware?
This is a term that is usually used to describe malicious software that are designed to do damage or execute unwanted actions on your computer system. Examples of malware include all the following:
- Viruses
- Spyware
- Trojan horses
- Worms
- Rogue security software
How To Protect Your Computer From Viruses and Malware

Getting rid of computer viruses or spyware can be tricky without the help of the right malicious software removal tools for your computer device especially because hackers and cyber-criminals have so programmed their malware such that most computer viruses and other harmful software automatically reinstall themselves after the viruses and malware are being detected and removed from your system. Luckily, however, by updating your computer regularly and by using superior malicious software removal tools like what Avast Free AntiVirus provides, you can now permanently get rid of any unwanted malicious software from your computer device.