As file-encrypting ransom Trojans are earning big bucks for their authors these days, the concept of ransomware kits, or Ransomware as a Service, has come on stage. About half a dozen of them emerged on the black market recently.
This trend has made it amazingly simple to become a cybercriminal. There is hardly any tech knowledge involved. Furthermore, ransomware kits are free. All it takes to start using one is to register, sometimes even without email, adjust a couple of settings, including the ransom amount and Bitcoin address – and that’s it, your custom payload is readily available, and you can get down to the spreading part. Moreover, the bad guys can even provide assistance with the distribution. Their forums advise on ways to rent botnets and order phishing campaigns on the darknet marketplace.
This is close to a perfect scenario for both parties involved: the would-be distributor who has no money and knowledge gets the malware for free, and the creators outsource the entire ransomware spreading part while subsequently gaining profit.
Below is a list of 6 kits which surfaced over the course of the past year.
1) Tox
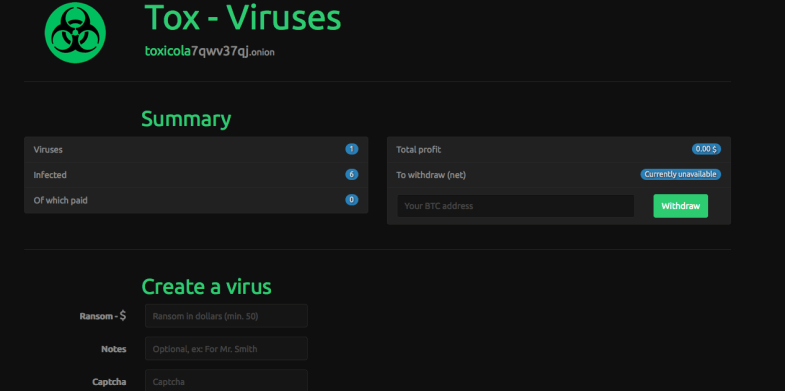
Tox was one of the RaaS pioneers. It was first spotted around in spring 2015. Tox is free to use. Anyone interested simply has to register on the dedicated website. User interaction and payments are based on Tor (The Onion Router) and Bitcoin, respectively. The authors take 20% of every ransom paid by victims. Tox is quite good at evading antivirus detection. The targeted users would need supplementary defenses (HIPS, sandboxing, whitelisting) to intercept or otherwise thwart the malware designed with Tox.
Creating a personalized version of the ransomware is a matter of going through as few as three steps: entering the size of the ransom to extort, defining the phony reason for file encryption, and typing the captcha. Ultimately, this workflow generates a 2MB executable masqueraded as a .SCR object, which the affiliates can then spread. The Tor-based site backing Tox will keep records of the installs and revenue. The share of earned money is sent to the specified Bitcoin address. According to expert analysis, the Trojan’s code is fairly primitive, which doesn’t make it any less efficient, though. As the security industry’s interest in Tox started to grow, the developer shortly admitted on the darknet forum that the circumstances were getting out of his hands. In the long run, the Tox web page went offline. According to some investigative reports, its author is a teenager.
2) FAKBEN
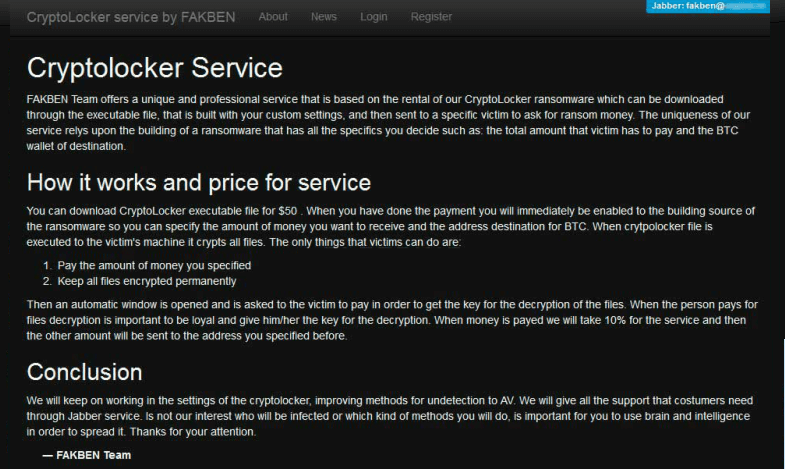
Wannabe cybercriminals can apply for the FAKBEN Team’s service and get a build of CryptoLocker ransom Trojan. As in the case of Tox, the payload gets generated according to the customer’s preferences. Unlike the kit above, though, this one implies an opening fee of 50 USD.
These individuals appear to have a code of ethics of some sort. They state on their web page that the private decryption key must be provided without fail in case the infected user performs the buyout. The FAKBEN operators take 10% of the ransom and submit the rest to the affiliate. This instance of Ransomware as a Service features an intuitive console that displays the accurate number of contaminated workstations and the ransom payments made. Additionally, FAKBEN can facilitate payload delivery via exploits that use vulnerabilities in software like Adobe Flash Player and Java. This is an extra feature that presupposes a separate payment. As per security insight, the FAKBEN Team is leveraging an encryption model similar to that of the Hidden Tear proof-of-concept ransomware.
3)Hidden Tear

This one stands out from the crowd. Utku Sen, a Turkish security expert, posted a completely viable ransomware code on GitHub. The malware called Hidden Tear uses AES (Advanced Encryption Standard) to lock down the victim’s files. The prerequisites for data recovery include the decrypter program and the private key, which can be obtained on condition that a ransom is submitted. It doesn’t cost a penny to use the Hidden Tear ransomware kit. The infection doesn’t get detected by commonplace antivirus suites. Furthermore, the executable is tiny, taking up as little as 12KB.
Importantly, there is a disclaimer on the GitHub page stating that Hidden Tear may only be used for educational purposes otherwise it can lead to legal prosecution. As we already know, however, the FAKBEN guys are using this code for purposes that are far from educational.
4) Encryptor RaaS
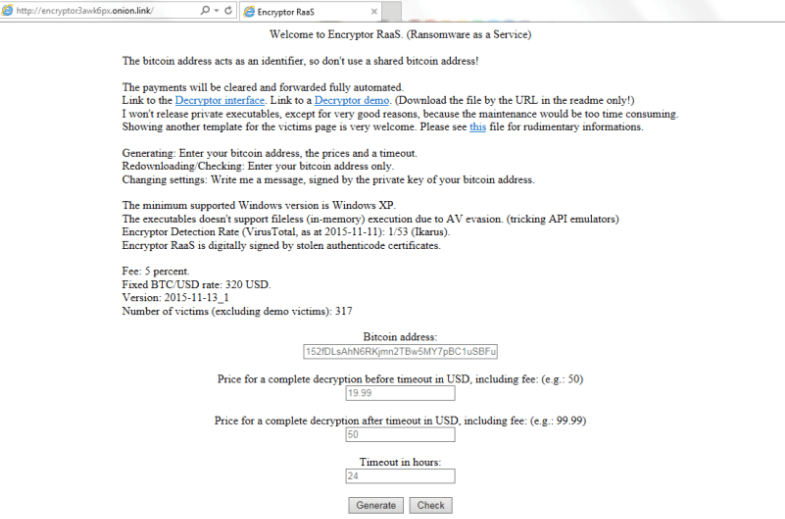
Predictably enough, this service is hosted on a Tor-based domain too. The publisher blatantly calls the kit Ransomware as a Service. The affiliate commission amounts to 20% of the gross ransom payments. All the associated financial transactions are based on the use of Bitcoin, which is a common approach too. It’s entirely up to the customer how the malicious file is distributed. The authors, in their turn, do the payment processing part, issue decryption tools and send the commissions after the fact.
The customizable parameters include the standard ransom size, the increased amount if the deadline isn’t met, and the timeout in hours. For the purpose of accurate tracking, every affiliate gets their unique Customer ID, which is integrated into the custom malicious executable.
5) ORX Locker
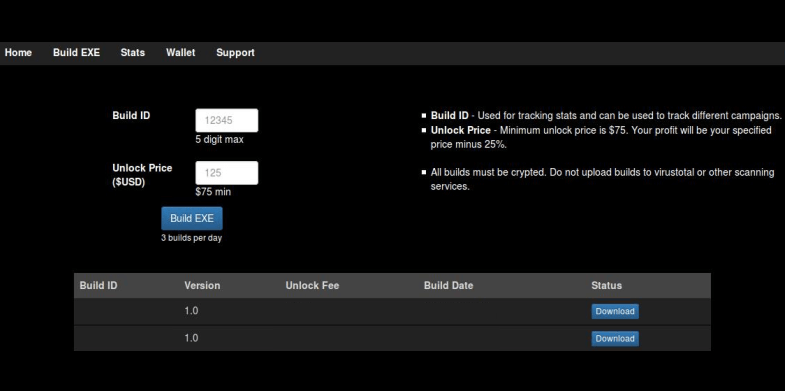
The RaaS implementation by Team ORX is quite run-of-the-mill: the hosting page only requests a referral name from new affiliates. To build the ransomware file afterward, the customer must enter the ID number of up to 5 digits and configure the ransom amount of 75 USD or higher. The Build EXE button then does the payload creation job proper, producing a ZIP file with the binary. The generated revenue can be transferred to a Bitcoin wallet at any time during the campaign.
The ORX ransomware goes a well-trodden path after it ends up on the victim’s computer: it encrypts personal files and displays a ransom note. When executed, the infection downloads the official Tor client onto the machine and routes its data over the respective secure gateway. The ransom Trojan assigns a unique payment ID to every victim and provides a personal onion link to the payment page. All ransoms are collected and processed by an intermediary entity that distributes the creator’s and the affiliate’s share in accordance with the predefined terms.
Unfortunately, antivirus products are not likely to catch ORX due to the obfuscation techniques it employs. Another interesting fact is that part of the plague’s C&C infrastructure is hosted on websites of some well-known educational institutions.
6) Ransom32
The makers of the first JavaScript ransomware on the loose stick with the RaaS model as well. Anyone who has a Bitcoin address can get registered on the dedicated Tor hidden server. The affiliate commission amounts to 75%, and the rest goes to the creators of Ransom32. The user-friendly administrative console allows the malefactor to set the buyout sum and configure the ransom notification that will be presented to victims. This dashboard also contains such options as locking the target system and keeping the computer’s performance unaffected during file encryption. Of course, real-time campaign statistics is displayed too, including the number of installs and the revenue in Bitcoins.
As opposed to most of its counterparts, Ransom32 is distributed in a fairly large WinRAR archive (22MB) holding the executable file. Interestingly enough, the payload package contains an executable camouflaged as the Chrome browser, which turns out to be NW.js application. The fact that the latter denotes a legit framework enables the threat to stay undetected by the conventional antimalware. Furthermore, JavaScript and HTML used in the code make Ransom32 potentially cross-platform, which means it is capable of compromising Windows, Linux and Mac machines alike. The crypto utilized in this attack is 128-bit AES.
Conclusion
The ransomware-as-a-service principle keeps delivering cybercrime to the masses. Unfortunately, it doesn’t take a rocket scientist to design a kit like that and do black hat business on a large scale. Since this model proved to be highly effective, the distributed malware is continuously morphing into new breeds.
When it comes to ransomware, diversified backup activities is the best defense strategy. Antimalware suites with built-in behavioral analysis modules are better than the conventional signature-based tools in terms of preventing ransomware onslaughts.
