TeslaCrypt is one of the latest file-encrypting ransomware programs made by hackers. It is a program that targets different operating systems including Windows XP, Windows Vista, Windows 7 and Windows 8. TeslaCrypt was first discovered around the end of February 2015, and later, a synonymous version called Alpha crypt was released at the end of April of the same year.
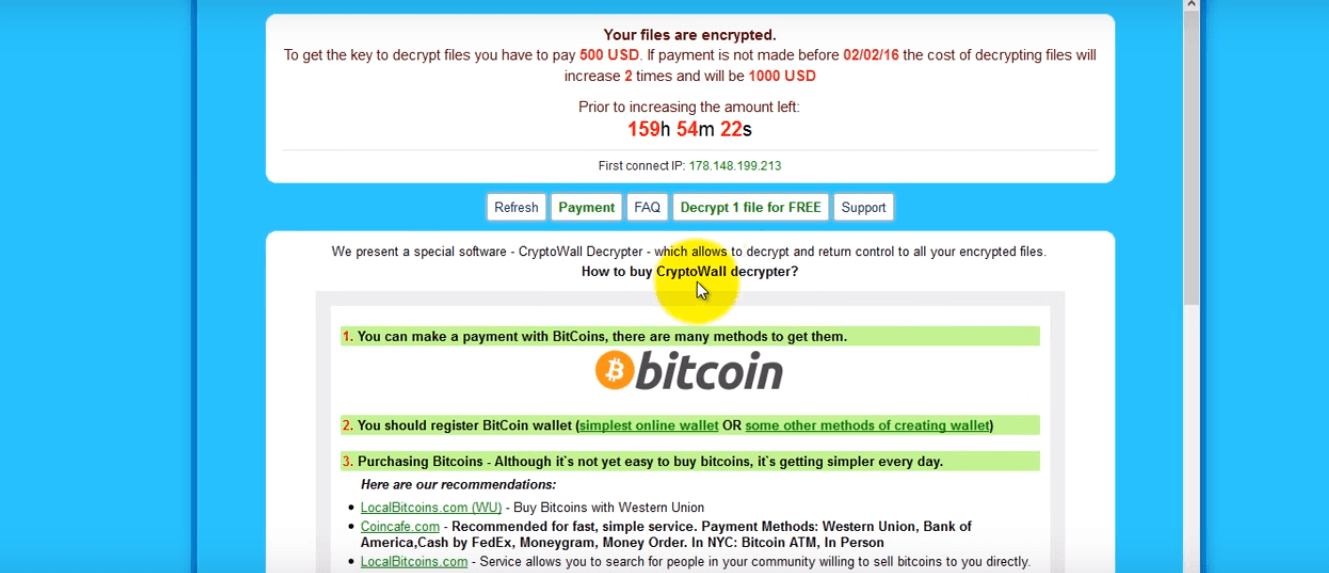
So, what happens when TeslaCrypt infects your computer? The program starts by scanning your computer for data files and then it encrypts them using AES encryption. Basically, what this means is you can no longer open any of your computer files. Once the infection has gone through your computer and encrypted the data on your computer drives, it displays an application with instructions on how to get your files back. These instructions take you to a decryption service that charges anywhere from $100-$1000 to fix. Payments are taken through bitcoins and in some cases PayPal, but the address for the payment differs for each victim. This is similar to paying a ransom, but for your data files.
When TeslaCrypt is first installed, it creates a random named executable in the%AppData% folder. This starts the launch and scans all of the drives on the computer for data files and starts to encrypt them. It then appends a new .mp3 and .micro file extension, although it can add some other extensions as well. When new versions of the hacking software are released, it uses different file extensions such as.ecc,.ezz, .exx, .xyz, .zzz, .aaa, .abc, .ccc.
Programs like TeslaCrypt are a new type of malware called ransomware. It is a lucrative method for cyber criminals to extort money from vulnerable users.
There are also other examples of ransoming, such as Cryptolocker and Torlocker, both which have extorted huge amounts of money from people all over the world. The stats offered by TeslaCrypt suggests that the programmers have made hundreds of thousands of dollars and shows us that ransomware is performing well as far as a criminal software goes, despite the growing awareness of the technique.
Research shows that the authors of this hacking software show little bias as to whom it targets, and also have been known to affect computers of students in Iran and Spain. The students, from fear of losing their valuable college assignments, find the money for the ransom. On the other hand, there are also small businesses and entrepreneurs that are unable or unwilling to pay, end up giving up their data as a result of the infection.
How Do I Keep Teslacrypt from Spreading to My Computer?
Teslacrypt uses an Angler Exploit Kit as its preferred distribution method because angler uses sophisticated techniques to avoid antivirus detection. But, TeslaCrypt also uses other distribution channels such as infected websites or malware ties in campaigns.
In a very real way, this is ransomware distributed at its best, as it uses different distribution channels. We’ve even seen it being spread via spam emails which contain a malicious zip attachment. When a user opens a zip file there is a .js file, which retrieves TeslaCrypt from a compromised webpage.
When the email arrives it appears to come from a company demanding to be paid for an overdue notice.
When the file is opened and while the user is reading the email, the malicious code connects to URLs and downloads the ransomware. The next step that the malicious ware concentrates on is to encrypt the data on the machine; including any networked computers within a system as well.
It can encrypt any and all files with the following extensions:
.r3d .css .fsh .lvl .p12 .rim .vcf.3fr .csv .gdb .m2 .p7b. rofl .vdf .7z .d3dbsp .gho type.m3u .p7c .rtf .vfs0 .accdb .das .hkdb .m4a .pak .rw2 .vpk .ai .dazip .hkx .map .pdd .rwl .vpp_pc .apk .db0. hplg .mcmeta .pdf .SAV .vtf .arch00 .dba .hvpl .mdb .pef .sb .w3x .arw .dbf .ibank .mdbackup .pem .sid .wb2 .asset .dcr .icxs .mddata .pfx .sidd. wma .avi .there .indd .mdf .pkpass .sidn .wmo .bar .desc .itdb .mef .png .sie .wmv .bay .dmp .itl .menu .ppt .sis .wotreplay .bc6 .dng .itm. MLX .pptm .slm .wpd .bc7 .doc .IWD .mov .pptx .snx .wps .big .docm .iwi .mp4 .psd .sql .x3f .bik .docx .jpe .mpqge .psk .sr2 .xf. bkf .dwg .jpeg .mrwref .pst .srf .xlk .bkp .dxg .jpg .ncf .ptx .srw .xls .blob .epk .js .nrw .py .sum .xlsb .bsa .eps .kdb .ntl. QDF .svg .xlsm .cas .erf .kdc .odb .qic .syncdb .xlsx .cdr .esm .kf .odc .raf .t12 .xxx .cer .ff .layout .odm .rar .t13 .zip .cfr. flv .lbf .odp .raw .tax .ztmp .cr2 .forge .litemod .ods .rb .tor .crt .fos .lrf .odt .re4 .txt .crw .fpk .ltx .orf .rgss3a .upk.
The files are then renamed and changed to other formats with other extensions; the headers are also changed and placed with a “blob” header. The ransomware proceeds to delete all local shadow copies and copies its own files to the directories. These include the directions on how to pay the ransom so that the victim can regain his data.
Also Read: Ransomware as a Service: 6 Discovered Instances
Do I Need to Pay the Ransom?
This is a decision only you can make, but we recommend that you not pay the ransom. There’s no real guarantee that you’ll receive the decryption key, and even when you do, there is a chance that your files will remain damaged.
Because the ransomware has been on the market for more than a year now, there are a few decryption tools that work at regaining your information. Still there are occasions that you just can’t decrypt your data safely.
How Do I Keep Teslacrypt from Infecting My System?
There are a few things you can do to help keep your system protected against all types of ransomware.
- Avoid keeping important information on a local drive – Backup all of your data to the cloud or to an external hard drive.
- Don’t download or open .zip attachments placed in the spam folder or in emails that come from unknown senders. Learn to identify spam emails and mark them as spam. Cyber criminals love to infiltrate your system through spam so try to avoid opening emails in your spam folder.
- Avoid clicking links that come in the spam email – These links redirect you to infected domains which host TeslaCrypt and other types of ransomware.
- Keep your software up to date – An updated operating system can reduce problems within your system by as much as 85%. Also, you will definitely want to use a good antivirus with the real-time scanner active. These may not be the first line of defense against ransomware, but they can keep the malware that brings such software programs out of your system.
- Keep a ransomware tool on hand to counter attack an infection quickly.
Conclusion
Ransomware like Teslacrypt is now a digital reality and its effects can be quite debilitating to both – individual users and companies around the world. Everyone needs to be prepared to handle such a problem, the best way being to know about this type of software and understand what you can do to prevent it. Being informed about this type of threat can help us be less vulnerable to cybercrimes.