An increasing number of cloud breaches are due to misconfigurations and human error. This is often due to unfamiliarity with cloud systems or insufficient security resources. Adopting cloud services can increase the complexity of your systems, making them harder to secure.
To make sure that your data is as secure as possible, it’s important to understand how to properly configure your resources. In this article, you’ll learn what security aspects you are responsible for in your cloud configuration. You’ll also learn some practices for ensuring that your system is secure.
Security Responsibility in Azure
Azure uses a shared responsibility model that varies according to the type of cloud services you are using. Your options include Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS).
Below is a breakdown of security responsibilities by service type:
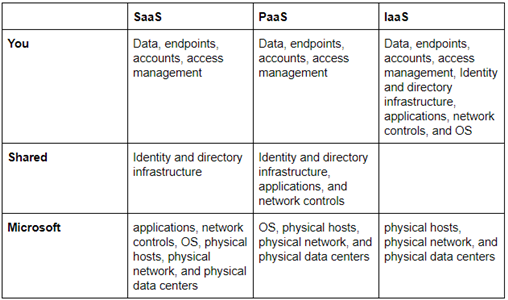
To secure the aspects that are your responsibility, Azure includes many built-in features and services. Some of these services are included with your account subscription while others cost extra. A full list of Azure provided services can be found here. You can also use third-party services, available either through the marketplace or through individual integration.
4 Practices for Securing Your Data in Azure
Each cloud configuration requires unique policies and tools for proper security. However, there are certain practices in common with all effective security plans.
1. Have a Recovery Plan
While having a recovery plan cannot protect you from a data breach, it can ensure that you retain access to your data. Having backups can enable you to restore systems quickly and easily after an attack or disaster. When creating backups, make sure to follow the 3-2-1 rule: 3 copies, 2 locations, 1 location off-site. Using this rule can minimize the chance of all backup copies being corrupted or deleted.
Azure provides a built-in service for backing up your data, called Azure Backup. With Backup, you can create automated backup policies and manage your copies from a centralized location. When considering this service, keep in mind that Azure backup does involve additional costs. Using this service as your exclusive backup solution can also limit your ability to restore data outside of Azure systems.
2. Encrypt Your Data
Make sure that your data is encrypted both in-transit and at-rest for maximum protection. At-rest encryption can help you ensure that data is only readable by those with the correct authorization. In-transit encryption can ensure that data isn’t intercepted or modified when accessed remotely.
At-rest, server-side encryption functionality is included with all Azure services. Keys for server-side encryption can either be managed by your services, managed by you with Azure Key Vault, or fully by you. Azure Key Vault is a paid service that can be used with most Azure services for centralized key management. If you choose to manage keys yourself, you are responsible for hosting them and performing appropriate configurations.
In-transit encryption is accomplished using SSL/TLS protocols. When accessing data through the Azure portal or via REST API, HTTPS is used to securely transfer information. You also have the option of accessing Azure via a Virtual Private Network (VPN). Using a VPN allows you to isolate communications from public networks for greater security.
3. Limit Data Access
Restrict access to your data using the principle of least privilege. This principle states that minimum permissions should be given to users, endpoints, or services. Use role-based permissions whenever possible. Doing so will disperse administrative privileges. Dispersal can reduce the amount of damage that can be done with compromised credentials.
Classifying data according to priority can help you identify how to distribute security resources. Classification can also help you quickly assess the impact of any attacks that occur. Once your data is classified, you should try to isolate critical data as much as possible. Using layered authentication can help restrict access. Layered authentication requires users to pass through several permissions gates before accessing data.
There are two natives, paid services that can aid you in classification and rights restriction. You can use the Azure Information Protection service to classify files. The service then identifies data priority in file headers, footers, and metadata. You can use Information Protection in combination with Azure Rights Management. With classification information, you can restrict file access regardless of location. This means that even if you email a file to an external location, your policies can limit access to authorized users.
4. Automate Your Monitoring
Public clouds are constantly connected to the Internet, leaving them vulnerable to a host of attacks. There are also vulnerabilities created by sharing resources with other tenants, which is the default in public clouds. To fully secure a cloud system, you need 24/7 monitoring and real-time analysis of log information. Automation is a cost-effective way to meet these needs.
Consider using a System Information and Event Management (SIEM) solution to centralize monitoring and automate detection and response. SIEM solutions often include machine learning algorithms that can identify threats quickly and effectively. These solutions enable you to define actions to be taken when a threat is identified, such as revoking user access. Once a SIEM has identified and responded to a threat, your security team can more fully assess and respond to the incident.
Conclusion
Securing your cloud properly requires research and dedication. You cannot simply move data to the cloud and expect it to be kept safe. Understanding your management and monitoring responsibilities, and learning basic best practices, are among the first steps to securing your cloud-based resources. As a next step, consider taking a look at the OWASP Cloud Security project, an open-source security resource. It can provide you with in-depth vulnerability information as well as some functional guidelines for security.