Instagram has had a bad couple of years. The app has been hit with a series of hacks, as well as revelations about the fact that private Instagram posts aren’t all that private.
Now, research has shown what we’ve long suspected: that Instagram is (by far) the most likely app to get hacked, and especially so if you own an iPhone. Even worse, the level of knowledge of the average consumer about how to defeat Instagram hacking remains very low.
In this article, we’ll look at the most recent research about just how vulnerable Instagram is, explain why the app has become such a target, and show you how you can use the app to protect yourself.
The Numbers
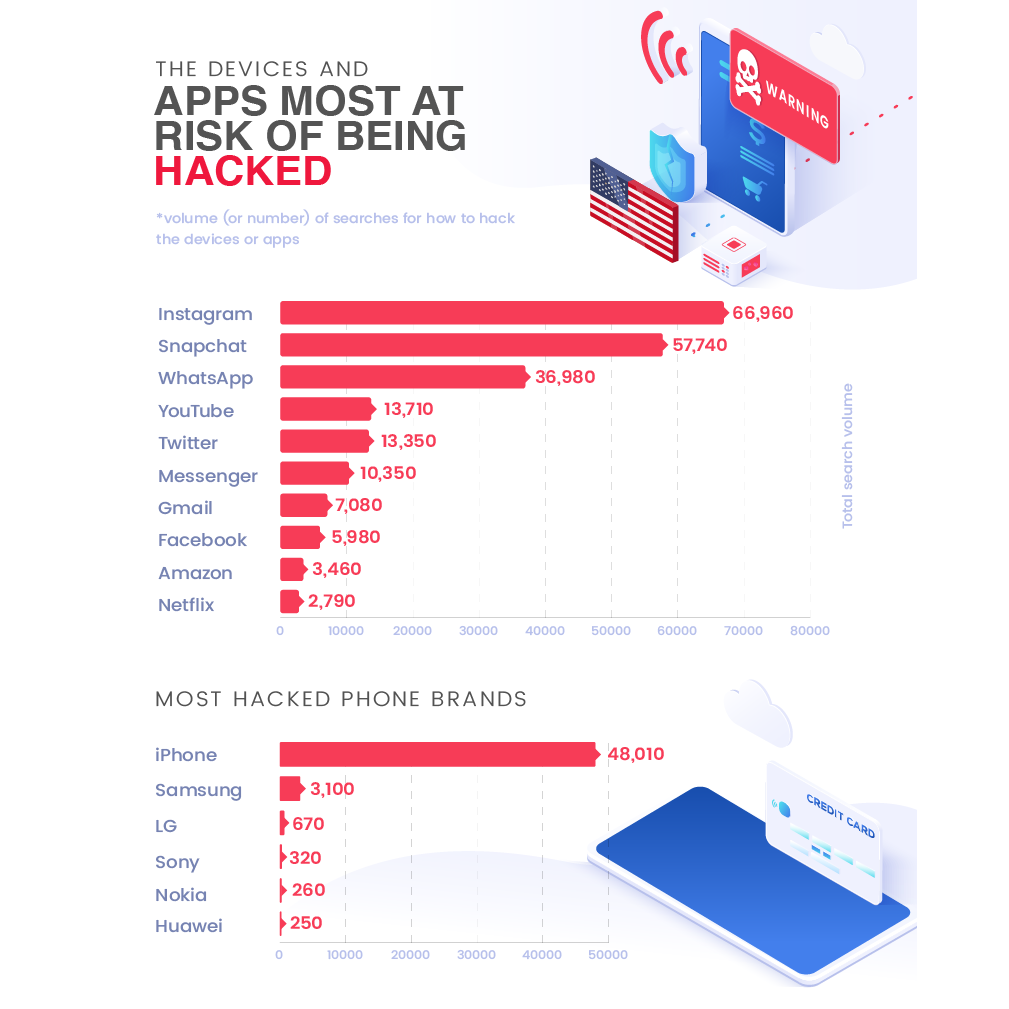
The recent research makes for shocking reading when it comes to just how much Instagram is targeted by hackers. This research is also interesting because it takes a novel approach: instead of just looking at how many hacks have been directed at popular apps, it also provides information on how many people have searched for information on how to hack them.
Across all of these metrics, Instagram is by far the most hacked app. The volume of searches for “how to hack Instagram” far exceeded the corresponding number for every other app tested, with Snapchat and Whatsapp coming second and third. The situation is even more unbalanced when it comes to searches for information on how to hack different phone brands: iPhones are searched for almost ten times as much as the second-most searched brand, Samsung.
Why Instagram?
This data raises some interesting questions about why Instagram is the most hacked app in the world. Collecting data on the number of people searching for information on how to hack the platform might be seen as less than useful because anyone using Google to search for “how to hack Instagram” doesn’t know how to do that. On the other hand, the raw number of hacks of the platform indicates that it remains the riskiest app on your phone. Why is that?
Well, there is a combination of factors. It’s telling, for instance, that all of the most commonly hacked apps make extensive use of cloud storage. Hackers, it seems, are betting on the fact that even tech giants don’t know how to ensure cloud security.
Secondly, Instagram is highly vulnerable to the most common types of cyberattack, and especially to phishing and other types of spoofing attacks, and especially when used over a public WiFi network. In other words, Instagram is targeted because it is easy to compromise.
Looking at another way, Instagram is a temptation for hackers because it is integrated with many other apps.
“Instagram as a company, prides itself on how well its app works with other parts of your phone’s ecosystem,” says Alex Williams of the Hosting Data web research group, “but in reality that represents a bad approach to cybersecurity. When protecting systems, we want to segment them, not allow hackers to move easily from one part to another.”
This is true not only of basic apps like the one that runs smartphone cameras, but also (in some cases) apps that contain financial information. Whilst gaining access to your Instagram photos is unlikely to be a lucrative outcome for hackers, getting access to your banking details may be. In short, it’s not the data stored in Instagram that makes it a target. Instead, the app is merely a back-door into other apps that store sensitive information for everyday people.
And considering the enormous levels of debt that most people in the US and UK are already in, with total household debt in the United States fast approaching $14 trillion, breaching even a small percentage of Instagram accounts can cause massive financial problems for those everyday people.
Protect Yourself
Protecting yourself against Instagram hacks involves doing the basics right. First, the interconnected nature of the Instagram app should be reduced as much as possible. Users should carefully check the permissions that they have granted to the app, and disable those that are not necessary for the way that they use it. Equally, they should avoid linking the app to their other devices: smartphone apps can be a source of malware infection, and Instagram more than most.
Secondly, a particular problem when it comes to making Instagram more secure is the fact that the app is used by so many young people. Having grown up in the information age, many Gen Z users simply don’t think about cybersecurity. For parents, the recent research is a reminder that they need to teach safety to their children at the earliest possible age. This should include a reminder that posting private information to Instagram is not a good idea.
Thirdly, online businesses should be very careful when relying on Instagram to make sales. Always rely on invoicing tools that come with PCI-DSS compliances, meaning that customer data will be kept encrypted and only shared with fellow employees on a need-to-know basis. Many hackers may attempt to ‘follow’ your customer after hacking into your Instagram account all the way to them making a sale, which is why using encrypted invoicing or payment processing services can help serve as a backup security measure.
The Bottom Line
Or, of course, you can take the most obvious conclusion from the recent research: don’t use an iPhone, and give strong consideration to deactivating Instagram. As with any popular devices or apps, they are likely to remain a major target for hackers in the coming years. Combined with the privacy intrusions that both Apple and Instagram are regularly accused of, this makes part of a compelling case to just stop using them completely.