Cloud computing is gaining popularity as organizations all over the world undertake to digitalize their operations and assets. However, before organizations can take advantage of on-demand computing services, they have to successfully migrate to the cloud.
This article will explain some key concepts of cloud computing, review the security risks that can occur during cloud migration and offer a few practices that will help you safely migrate to the cloud.
What Is Cloud Computing?
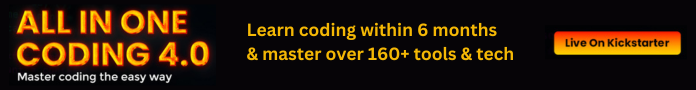
Cloud computing is a model that offers computing resources as services hosted over the Internet. Cloud vendors take on the responsibility for setting up and maintaining physical data centers, offering their computing resources as services to cloud users. Cloud users are charged on demand and can grow at scale as they continually adjust the pricing based on use.
There are many service models, each offering different resources to cloud users. There three most common service models are referred to as SPI, which stands for Software, Platform and Infrastructure. Here’s a brief review of what each SPI service means:
S—Software as a Service (SaaS)—delivers software under specific licenses, such as CRM and email, over the Internet. SaaS is a product you consume.
P—Platform as a Service (PaaS)—delivers application and data resources, such as operating systems and execution environments, over the Internet. PaaS is used as building blocks.
I—Infrastructure as a Service (IaaS)—delivers virtualization, servers, storage, and networking resources over the Internet. IaaS is what you migrate your digital assets to.
It’s important to note that each service tier differs not only in the resources it offers but also in the way it distributes the responsibility.
If on-premise data centers put all of the responsibility on the consumer, cloud models distribute responsibilities between vendor and consumer. IaaS simplifies in-house computing management, PaaS reduces application development tools, and SaaS eliminates desktop software licensing installations and complications.
What Is Cloud Migration?
Cloud migration is the process of moving some or all of your digital operations to the cloud. Today, there are many cloud architectures, some of which are more complex than others. Before migrating to the cloud, it’s important to identify your needs, create an inventory of your resources, assess cloud vendors, assess your skills and choose an architecture accordingly.
There are three main types of cloud migration:
- On-premise—migrating from on-premises data centers to the cloud
- Cloud-to-cloud—migrating from one cloud vendor to another
- Reverse cloud—migrating a cloud service to an on-premise data center
The most important element to the success of a cloud migration operation is careful and strategic planning. There are many cloud migration strategies, which we won’t discuss here. Below, you’ll find a review of the top cloud migration risks and the best practices that will help you secure your assets during the migration process.
Top Security Risks of Cloud Migration
Planning ahead is vital for the success of any technological implementation. This is especially true for the security of cloud migration processes. During the migration phase, your data is in transit, which makes it vulnerable to attacks.
Most threat actors of today are automated bots, which are sent in unfeeling pursuit of your assets. The bot doesn’t care about your migration strategy, it cares about the security protocols, and how well they protect your data.
When you plan your cloud migration operation, expect the following threats:
- Exploitation of APIs—Application Programming Interfaces (APIs) serve as communication channels between environments. You will use APIs during the migration. Protect them at all cost.
- Blindspots—migrating to the cloud means giving up control over some aspects of your operations. Before migrating, check what security is covered by the cloud vendor (your blindspots) and what security you’ll need to cover (your windshield and mirrors).
- Data loss—cloud migration involves the transfer of data. Before migration, ensure that your data types and data structure have an exact match in the cloud. Otherwise, you’ll risk the corruption or deletion of your data.
- Theft of sensitive information—threat actors use sensitive information to commit identity fraud, gain access to accounts, and initiate more attacks. They will go after your information during the migration. Protect your data with encryption and VPN tunnels.
- Cloud outage—occurs when a cloud service is unavailable for use. That can happen due to power outages, Distributed Denial of Service (DDoS) attacks and any number of networking, software or IT issues. Backup every single byte you migrate. Otherwise, if an outage happens during the migration process, you’ll lose everything.
How to Safely Migrate to the Cloud—A Cheatsheet
Phase I: Plan for Success
- Assess your operations
- Assess your skills
- Create an inventory of your assets and environments
- Create a list of licensing and compliance requirements
- Set a budget for the migration and for the new cloud operation
- Research cloud vendors
- Create a cloud architecture
- Choose a cloud migration strategy
- Define what are the vendor’s security responsibilities
- Define your security responsibilities
Phase II: Plan for Failure
- Assess cloud migration threats
- Create a P&P that outlines the security policies and procedures that should take place before, during, and after the cloud migration
- Backup all the moving assets
- Encrypt all the data
- If you’re moving financial data, you MUST tokenize to maintain compliance
- Configure authentication and authorization protocols
- Set up disaster recovery in place
Phase III: Plan for Attacks
The last layer of security will vary greatly between one migration operation to another. There are many solutions to choose from, some of which are open-source, and some are paid services you can apply according to your budget. Here are some options for you to choose from:
- OpenVPN—OSS for building VPN tunnels
- AWS Direct Connect—for creating dedicated network connections between AWS and your assets
- Web Application Firewall (WAF)—scans for threats
- Intrusion Prevention System/Intrusion Detection System (IPS/IDS)—monitors malicious activity
- Cloud Access Security Broker (CASB)—enforces policies that mediate between cloud vendors and cloud consumers
Conclusion
Cloud migration is a complex, but worthwhile, operation. Many things could go wrong, and threat actors will take advantage of anything to get ahold of your assets. Try to plan ahead for as many eventualities as possible.
Many cloud vendors provide security controls, but they don’t cover all your security needs. Strategic thinking will help you choose the security procedures and solutions that fit the needs and scale of your project. Remember, there are many solutions that could be considered optional, but some measures, like backup, are absolutely necessary.